 Remember the great con-artist, Gregor MacGregor, known as the “king of all con-men?” He convinced people to invest in an entirely fictitious country that he had conjured up. More recently, remember Bernie Madoff, the con-artist who made off with more than $65 billion of investors’ money in a ponzi-scheme?
Remember the great con-artist, Gregor MacGregor, known as the “king of all con-men?” He convinced people to invest in an entirely fictitious country that he had conjured up. More recently, remember Bernie Madoff, the con-artist who made off with more than $65 billion of investors’ money in a ponzi-scheme?
In the past, great con-artists only preyed on the rich and famous, but that’s changed. New modern-day con-artists come in the form of hackers using social engineering tactics to steal the money and identities of regular people every day.
A recent example, the Google Docs phishing scam, made it appear that a contact emailed you asking you to open a Google Document. If you open it, hackers can get access to your information.
Social engineering has become so commonplace that victims seldom know they’re being targeted until it’s too late and they’ve already compromised their financial or personal information. On average, personal victims lose $4,187 in social engineering attacks while businesses on average lose $42,546.
Social engineering is defined as an act that influences a person to take an action that may or may not be in their best interest.
We’re sharing some tips for identifying social engineering attacks and how you can protect yourself, your staff and your practice.
Social engineering techniques have become increasingly sophisticated. They can easily look legitimate and lead people to clicks.
Commonly referred to as phishing, emails are the most common and the most successful form of social engineering. At Netgain, we’ve become increasingly vigilant about phishing as the incidents have skyrocketed. With 294 billion emails sent each day, phishing represents 77 percent of all social engineering attacks. Fraudsters send emails mimicking banking institutions or other well-recognized businesses and place malicious links within the email or request confirmation of personal information. Currently it’s common for hackers to use shipping notifications that look like they are being sent by reputable organizations or the names of leaders within the organization, namely the CEO or president to trick employees of that organization, as shown in these examples.
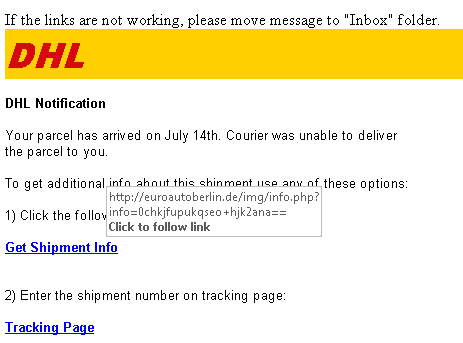
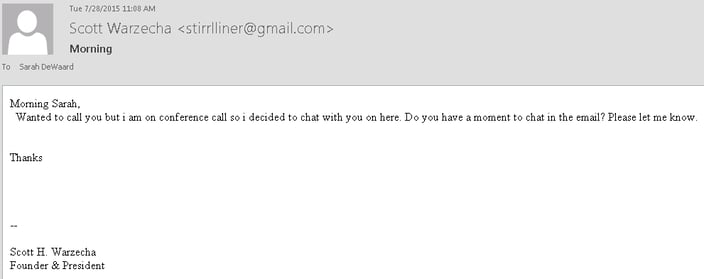
Such phishing attacks happen millions of times per day and unfortunately, because of improper education and vigilance, people sometimes do not pay attention to simple details and fall victim to these attacks.
Protecting your practice
- Educate, educate, educate
The proverb “a chain is only as strong as its weakest link” describes an organization’s vulnerability to social engineering. If an employee clicks on a malicious email or provides account information erroneously, your whole organization can be compromised.
Staff training is the single most effective defense against social engineering attacks. Educate your staff on new threats as they come up, ensuring they’re alert and know what to be aware of.
As it relates to email, ensure your staff knows how to identify a suspicious email. This can include the “from” line, links that lead to unsecure sites or requests for account information. If they receive a suspicious email, direct staff to send the email, via an attachment, to your practice’s security officer for further investigation. If identified as a threat, screenshot the email and alert the rest of the staff to watch for similar emails. - Enforce password policies
This seems like a no-brainer, but so many people and organizations make password mistakes that make them vulnerable to attacks.
Employ password policies that reduce your staff and practice’s vulnerability. For instance, do not use the same password for multiple websites. Doing so will make your accounts even more vulnerable if one of them is compromised. Also, mandate complex passwords within your practice. A complex password includes an uppercase, lowercase, number and symbol. Hacking these passwords are far more difficult than non-complex passwords.
Password tools like KeePass, 1Password or LastPass can help you manage the credentials for the many sites you access every day, while still employing strong passwords. - Consult with your IT partner
While human error is your greatest threat to social engineering, your IT partner can also help ensure that user error does not infiltrate your network.
Having your ePHI in a cloud environment can help reduce your vulnerability to social engineering. If a user opens an email or clicks on a malicious link, your cloud partner should have layers of security in place to ensure that malware does not get installed.
Even though you’re more secure in a hosted environment, your staff is still your greatest threat, which is why we urge to educate, educate, educate! Discuss with your IT partner how their security layers protect your practice from social engineering.
The threat of social engineering is real and needs to be addressed, and addressed often, within your practice. Educate your users on popular scams, how to detect social engineering attempts, and what to do if they believe they’ve compromised themselves or the practice.
 Support
Support Contact Us
Contact Us



